Scan Tool For Mac Address Linux
3 great scanner tools for Linux. 3 tools that make scanning on the Linux desktop quick and easy. 23 Sep 2014 Scott Nesbitt Feed. And The GIMP didn't have all the features of the ScanSnap Manager software (which is for Windows or Mac only), the ScanSnap did scan documents very quickly. The ARP Scan Tool (AKA ARP Sweep or MAC Scanner) is a very fast ARP packet scanner that shows every active IPv4 device on your subnet. Since ARP is non-routable, this type of scanner only works on the local LAN (local subnet or network segment). The ARP Scan Tool shows all active devices even if they have firewalls. Powerful: Nmap has been used to scan huge networks of literally hundreds of thousands of machines. Portable: Most operating systems are supported, including Linux, Microsoft Windows, FreeBSD, OpenBSD, Solaris, IRIX, Mac OS X, HP-UX, NetBSD, Sun OS, Amiga, and more. The tool can also scan for general information and vulnerable software packages and possible configurations flaws in the system. Lynis is commonly used by the system administrators and security penetration testers to perform audits and assess a system’s security.
Snipping tools for Mac. Mac OS has Grab built in. Grab is a snipping tool-type utility that can capture the screen complete with cursor. Find it in Applications and Utilities. It has the ability to select active windows, drag to select and use a timer to allow you to set up a. How can the answer be improved? Best Snipping Tool for Mac If you want a snipping tool packed with additional features, download Skitch, from the creators of Evernote. Skitch is a free snipping tool app for Macs that also allows you to easily draw arrows, boxes, add text, resize the image, and much more. 
- Scan Tool For Mac Address Linux Command
- Linux Get Mac Address
- Scan Tool For Mac Addresses Linux
- Mac Tools Diagnostic Scan Tool
- Ip Scan With Mac Address
The ARP Scan Tool (AKA ARP Sweep or MAC Scanner) is a very fast ARP packet scanner that shows every active IPv4 device on your subnet. Since ARP is non-routable, this type of scanner only works on the local LAN (local subnet or network segment).
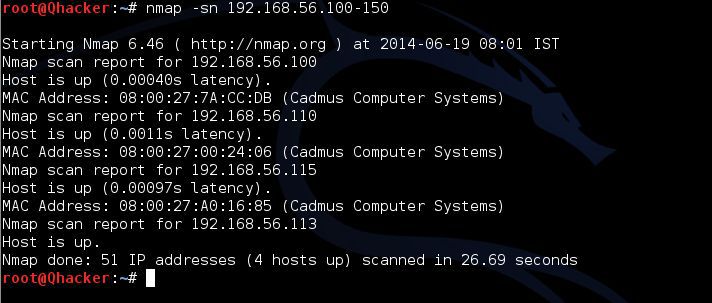
Env- Centos 7 , nmap 6.40
Currently I'm trying to fetch MAC/HW addresses for few list of IP's via nmap command utility and with root user its working perfectly.
As root user
Starting Nmap 6.40 ( http://nmap.org ) at 2018-06-19 07:05 EDTNmap scan report for 192.168.xx.xxHost is up (0.0015s latency).MAC Address: XX:XX:XX:XX:XX:XX
As non-root user
Warning: You are not root -- using TCP pingscan rather than ICMP
Starting Nmap 6.40 ( http://nmap.org ) at 2018-06-19 07:19 EDTNote: Host seems down. If it is really up, but blocking our ping probes, try -PnNmap done: 1 IP address (0 hosts up) scanned in 2.01 seconds
Requesting your suggestion/help how the same to be achieve via normal user.
Thanks
2 Answers
It is possible to run nmap as non-root user. This Wiki describes pretty good how to set everything up to run it as an unprivileged user. The linked tutorial also describes this for Ubuntu and Red Hat systems, which should be good for you since you are on CentOS.
I think it is important to keep this security warning in mind:
WARNING: This is dangerous. The Nmap Scripting Engine (NSE) allows scripts to sniff the network, change firewall roules and interface configuration, or exploit vulnerabilities including on localhost. It's possible, especially with elevated capabilities, for a clever person to use Nmap and NSE to escalate to full root privileges. If you do not understand these risks, do not do this.
Summary from the Wiki:
1. Restrict access to certain groups, for example adm. Make sure that you use the right location of nmap. In my case, this was /usr/bin/nmap:
2. Make sure the setcap command is installed (more information about capabilities here):
3. Sophos removal tool for mac. Now, set the capabilities. Once again, make sure to use the right location.
4. Finally, you are able to run nmap as unprivileged user. But, you have to explicitly define that you want to do so. You can define it as an argument of nmap
or as an environmental variable:
Edit: I don't exactly know why this answer is being down-voted since this is one possible answer to the question (although the question is of course better suited for Super User or Unix & Linux Stack Exchange). I added the results from my own systems with and without --privileged below:
Scan Tool For Mac Address Linux Command
Nmap must be run as root in order to retrieve this information. Fortunately, there are other sources of MAC address information on a Linux system: the system's ARP tables. After making an attempt to contact an IP address (either using Nmap or some other tool like ping), run arp -n to print the table of IP-to-MAC address mappings.